Users of computers began to threaten the publication of personal videos and browser history
 Source:
Source:Computer Users around the world have started to receive e-mails from Scam to extort money. Depending on who sent the letter, its contents may change. However, colleagues from Business Insider was able to extract common features in the letters of swindlers and find a way to protect yourself from them.
Typically, a new e-mail scams contain the following information:
the- Information that this password was used to crack the computer, installation it malware and tracking using web camera. the
- the Threat to provide a record with the webcam and the history of visited adult sites to relatives, friends and other contacts in case of non-payment of funds in bitcoins totaling about 1200-1600 dollars.
Your password that you ever used. the
Such a letter can really scare because one of your passwords is likely leaked at the time of some of the popular service. But the truth is that most of the scammers do not have access to your web camera, and contacts. Most likely, they have only one of your passwords and email address. Of course, if you don't use the same password for different services, which do not strongly recommended.
Bleeping Computer report that some scammers have earned more than 50 thousand dollars in this way. These data were obtained on the basis of analysis of bitcoin wallets. But experts in the field of security believe that most likely, you have nothing to worry about. The fraudsters are not aimed at you, but mailing is automated. Here is what it says about the situation Brian Krebs, a leading journalist in the field of security:
I assume the scammer has created some script that uses user names and passwords leaked from the popular web site a few years ago, and that each victim received a letter that used the same email address to log on to a compromised web site.
Indeed it seems that the crooks are using a very old password. Maybe the victims for several years do not use them. To not be afraid of fraud, you need to use long and different passwords. To simplify the work with them there are specific password managers.
Recommended
Is it possible digital immortality and whether it
when will man become immortal through digital technologies. I don't believe it. And you? In 2016, the youngest daughter Jang JI-sen This died of the disease associated with the blood. But in February, the mother was reunited with her daughter in virt...
Why bad long sit at the computer and how to fix it
I've recently conducted a small survey among friends and acquaintances about how they evaluate their effectiveness when working remotely. Almost everyone I know — now work from home with computer and phone. And, as it turned out, even those who...
Parametric architecture: can artificial intelligence to design cities?
When you think about the future, what pictures arise in front of your eyes? As a lover of retro-futurism – a genre which is based on representation of the people in the past about the future, I always imagined the city of the future built buildings, ...
Related News
7 laptops for those who want to buy the best
If you want to buy the most efficient laptop today, you need to look at the model with a premium design and materials, high-resolution display, processor and 16 gigabytes of RAM. In this case, you have the choice not too big. Here...
The hacker stole the files of the U.S. army, but could not sell them even for $ 150
the Hacker has guessed to use the vulnerability of routers to gain access to the files of the U.S. army. The obtained data he attempted to sell on the forum on the darknet, but was unable to find an interested buyer, even reducing...
Secret "pocket" Surface from Microsoft is with a folding screen
Microsoft is working on a mysterious new device from the Surface has at least a few years. The device, codenamed "Andromeda" was repeatedly flashed in patents, reports, references in the operating system, and should include design...
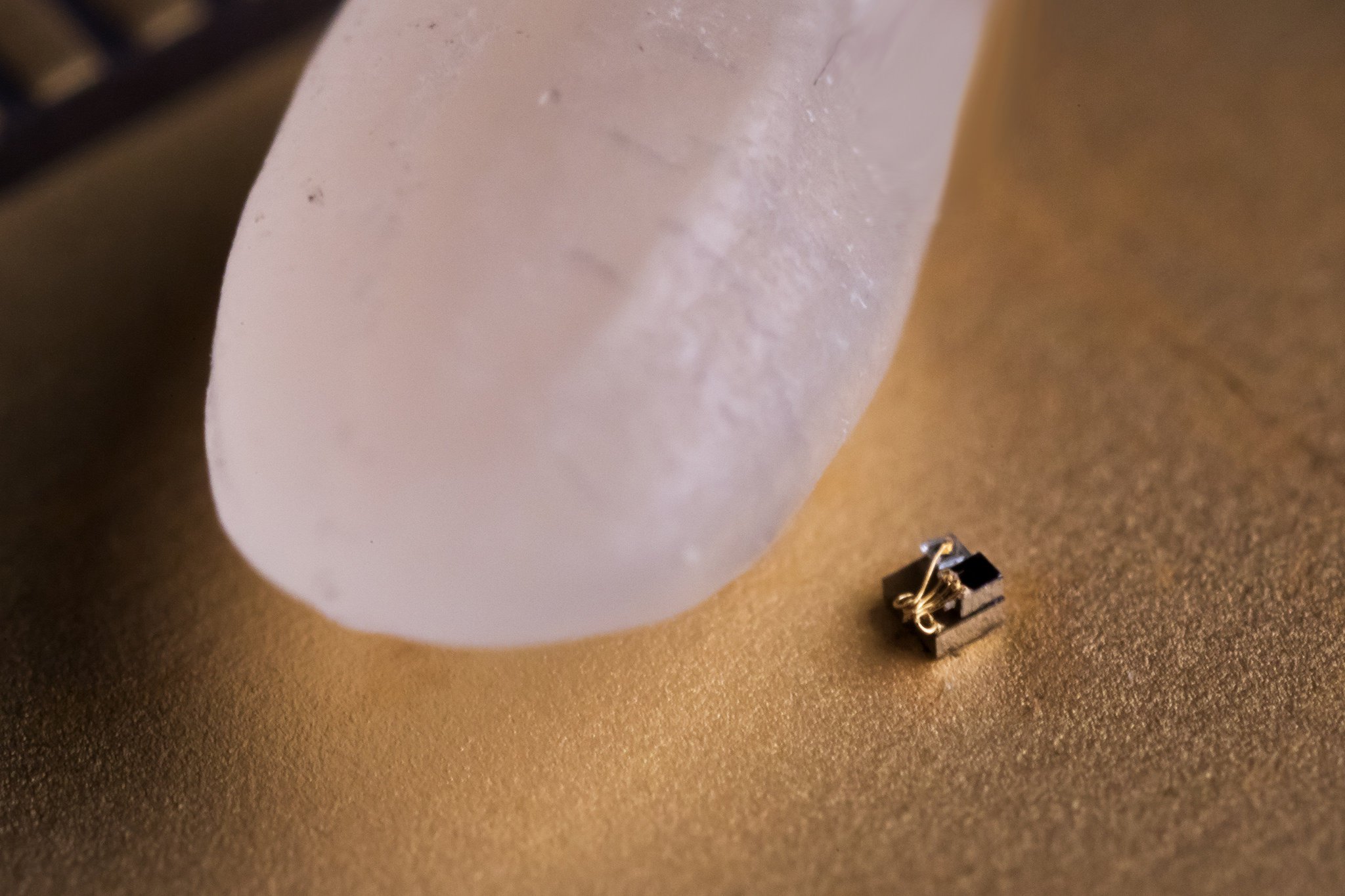
The smallest computer in the world has become even smaller
When IBM said in March that created the smallest computer in the world, scientists from the University of Michigan with displeasure raised eyebrows because IBM is the championship belonged to them. Now the smallest computer in the...
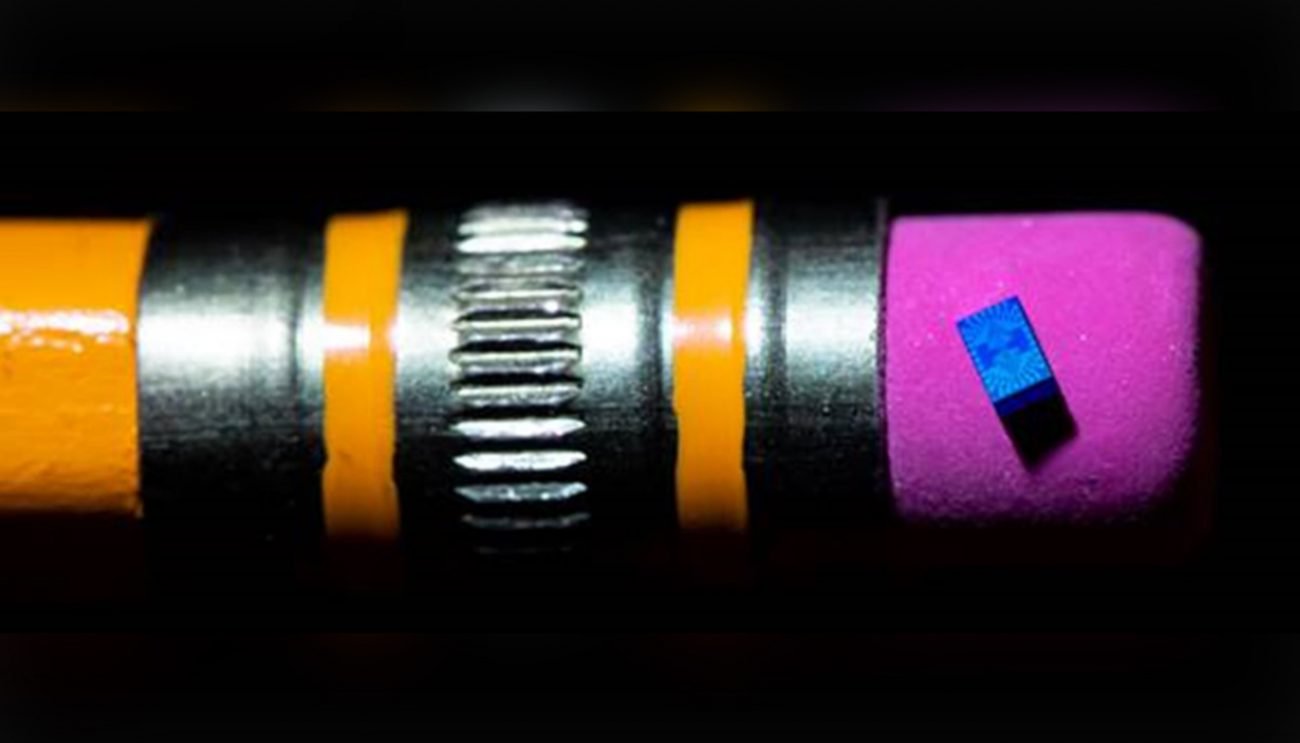
Intel has created the world's smallest quantum chip
Already practically does not remain doubts that in the future quantum computers, if not will replace the familiar to us computers, then certainly strongly they will press. The success in this sphere do have a company and recently,...
In the United States represented the most powerful supercomputer in the world
the US Department of energy introduced the world's most powerful supercomputer, selected the title from the Chinese Sunway TaihuLight. Peak performance supercomputer American Summit reached 200 petaflops. (200 quadrillion calculat...
HAL 9000 will never appear: emotions are not programmed
HAL 9000 is one of the most famous cinematic artificial intelligence. This superior form of intelligent computer malfunctioned on the way to Jupiter in the iconic film, Stanley Kubrick's "Space Odyssey 2001", which is currently ce...
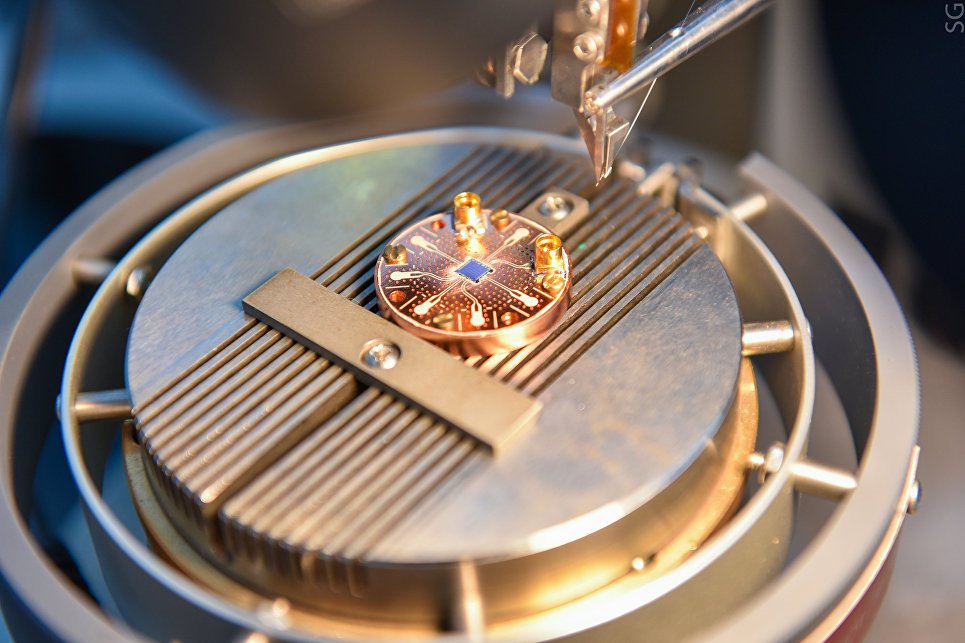
Developed a fundamentally new type of qubit for a quantum computer
an international group of scientists, consisting of Russian, British and German experts in the field of quantum technologies has created a revolutionary technology of qubits based on dzhozefsonovskikh the transition that represent...
Every Monday in the new issue of «News high-tech» we summarize the previous week, talking about some of the most important events, the key discoveries and inventions. This time we will focus on the toothbrush for mining,...
New Russian supercomputer called "talker"
On the territory of Russia operate more than ten supercomputers, the leader of which is considered to be . Its performance is more than 2 petaflops, which provides him 63rd place in the ranking of most powerful supercomputers in t...
Employees of "Kaspersky Lab" found unkillable computer virus
Almost every day on the world wide web to discover some new computer viruses. And very seldom happens so that viruses cannot be destroyed. Moreover, a rare virus is able to hide the years, from anti-virus developers. But, accordin...
Why is the AI still not mastered the translation languages?
In the myth about the tower of Babel the people decided to build a tower city that would get to heaven. And then the Creator realized that nothing would deter people and imagines they are not worth the bother. Then God created dif...
Serious quantum computers are ready to use. What they can do?
In a small laboratory in the lush countryside about a hundred miles North of new York city from the ceiling hangs a complex tangle of tubes and electronics. Is a computer, albeit messy. And it's not a regular computer. Perhaps it ...
Windows 10 in the new mode longer to save energy
the more difficult task — the more it will take energy. But the modern computing device, being very powerful, also often work from the battery. And there is a need to save energy. We are talking mostly about laptops, tablets...
Intel is developing spin qubits operating at higher temperatures
Intel continues to invest in new technology, and one of her latest interests — quantum computation. Last fall presented the first quantum processor on the basis of 17 qubits, and at the last CES, one of the largest manufactu...
In Russia will create a 50-Kubany quantum computer
the Foundation for advanced studies, Moscow state University, WEB and a number of other Russian organizations formed a consortium whose purpose is the development of a quantum computer consisting of not less than 50 qubits, said t...
Acer began selling "the lightest notebook" Swift 5 in Russia
In Russia started selling the new Acer ultrabook Swift 5. According to the company, the laptop is made of special alloy, which explains its light weight device weighs less than 1 kilogram. 14-inch laptop equipped with latest Intel...
Apple is planning to release a budget MacBook
In recent years, Apple has actively updated its flagship MacBook Pro laptop, forgetting about the line of Air. However, according to the latest reports, this year Apple company can finally get back to producing miniature laptops. ...
You need to open the "black box" artificial intelligence, until it is too late
For several years in the 1980-ies of the students of the Medical school of St George's hospital in London were selected using high-tech method. A computer program, one of the first of its kind, looking through resumes, choosing fr...
Turned off auto update Windows 10? In jail!
Windows 10 Operating system has many different features and capabilities, to understand which is sometimes very difficult. However, users of this OS say that one of its main drawbacks is the forced download of all updates and thei...

































Comments (0)
This article has no comment, be the first!